I2P Browsing Functions
This post relates to using the I2P Java software and using the I2P in Private Browsing Mode Firefox extension.
I2P
Community Product Development: Can We Bridge the Funding and Adoption Gap For FOSS Tools?
Within the internet freedom community we often struggle with funding support for free-open source tools. Teams are often small, overworked,
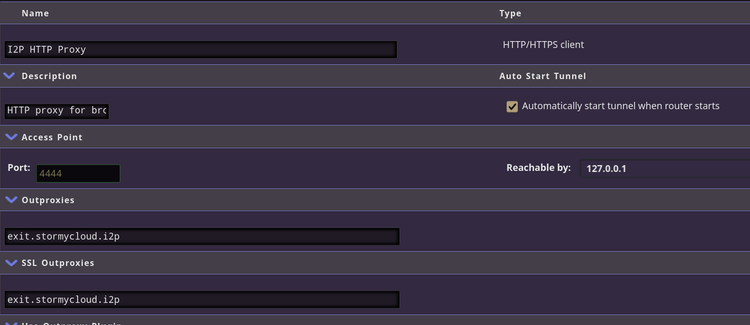
Meet Your Maintainer: A Conversation with I2P Outproxy Operators StormyCloud Inc.
Who is StormyCloud Inc?
Mission of StormyCloud Inc.
To defend Internet access as a universal human right. By doing so,
Meet Your Maintainer: DIVA.EXCHANGE
In this second instalment of Meet Your Maintainer, I reached out to Konrad from DIVA.EXCHANGE to talk about DIVA’
Introducing I2P To Digital Trainers: Revealing Gaps In Usability and Onboarding
In this last part of our interviews with the digital security trainers, we will share the impressions that people provided
Trust Modelling: Trust Supports Adoption and Informs Standards For Future Privacy Tool Development.
We asked the Digital Security Trainers what makes them trust a privacy tool. We left the word trust open to
Dear Privacy Tool Builders, I Just Need To Do My Work
This is the second part of a series where we share the insights from our community outreach earlier this year.
Ask A Digital Security Trainer: The Process of Risk Assessment
As part of our sustainability and adoption work, the I2P Research and Usability Lab has reached out human rights defenders,
About
Our goal is to support I2P network builders, participants and interoperability within the overlay network community.
Terms
All services listed