I2P Network Attack: A Summary
What is a DoS?
A denial-of-service (DoS) is an attack that attempts to disrupt the normal function of traffic on a network or server. When successful, it leads to traffic congestion and the inability to reach servers or services.
Traffic analysis will show information like spikes or odd patterns in traffic, floods of traffic with similar characteristics.
What is a Sybil Attack?
A Sybil attack is characterized by an attacker using spam on a network with nodes so that it can subvert a network's reputation system. The reputation system provides rules about expectations for interaction and roles in the network, like what sort of handling of information nodes participate in and how that information is distributed for network function. Feedback is required within the system in order to sustain and guide trust.
What Happened To I2P?
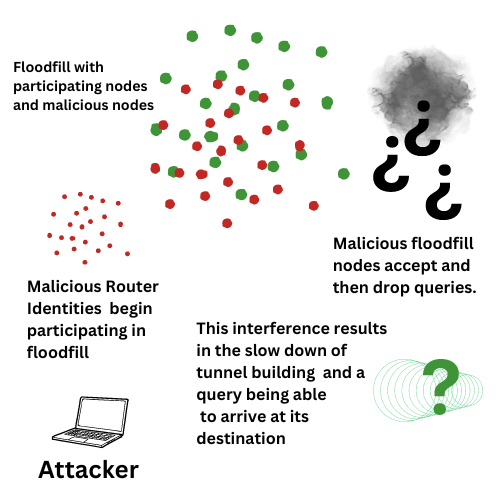
On February 5th, initial reports of floodfill spamming were reported within the I2P IRC community. Metrics showed spikes in new routers joining the network, and floodfill numbers within peer stats. These new routers were finding ways to become floodfills, and were were fielding and then dropping requests leading to tunnel creation rates dropping severely.
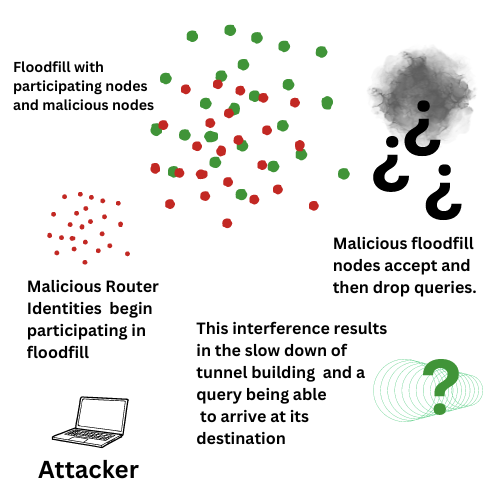
The floodfill function in the I2P network is comprised of routers that participate in distributing information. These routers act like switch boards - they accept netDb stores ( this includes router identity and initialized transport connection information) and respond to netDb queries. They get a message to its destination using the correct directions. For instance, if a router is firewalled it may use transports differently that if a router is not.
In early versions of I2P, the role of floodfills was performed by only three routers. Over time the design and implementation was replaced to allow the network to scale, and avoid the three floodfills being overloaded.
What people were seeing was that the network database had filled up with non participating floodfill routers, and network traffic was slowing. Tunnels could not be created because there was no information that was being passed to even be able to create them.
This means that queries were being hung until a properly participating floodfill router could pick up the the query and provide the information needed to proceed with tunnel building information. Success for visiting a destination was slow or in some cases not possible without trying several times.
Response Handling
I2P developers are and will be working through discovery and identification as the attack continues. Having used the Sybil detection tool, I can see changes in my own core Java router performance over the past few weeks.
Attacks are a part of any network threat surface, and thankfully the I2P network has existing tooling in place that is allowing it to adapt. Function has deteriorated at times, and in different ways depending on the distribution, but the network has remained usable.
This is a good reminder that the I2P network is relatively small, and that its stability and scalability will be tested not just with attacks, but also with growth and utility. Thanks to everyone who is testing, contributing, and supporting the network!