Overlay Networks x OPSEC: Encryption and Transports Are No Match For Footguns
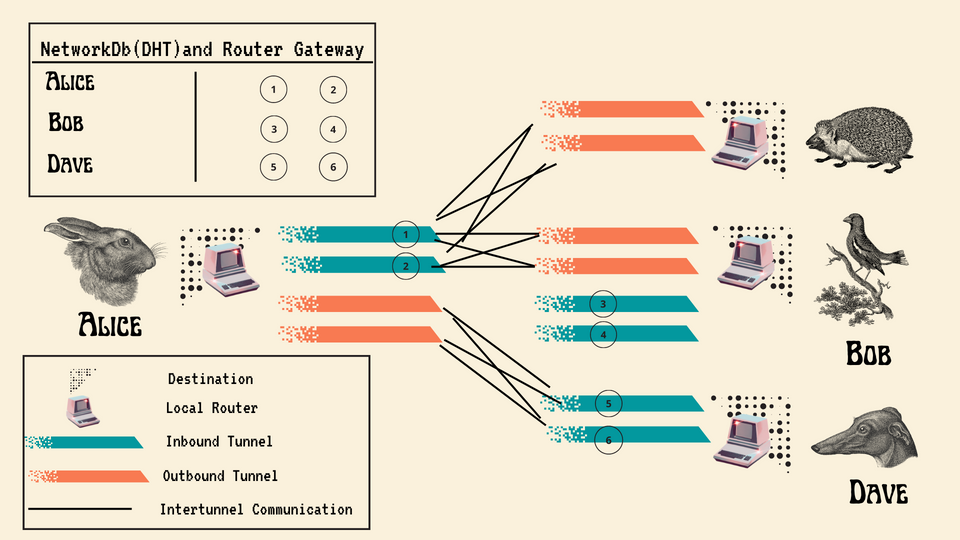
When people talk about the I2P network, the word they most often use is “privacy.”
When I write about privacy in the context of the I2P network I say “privacy by design.” This is meant to direct people to the engineering efforts that comprise the network in its protocols, transports, and how messages are encrypted in the I2P tunnel layer.
All of these functions support the goals of protecting the contents of messages within the network and providing blocking resistance.
There are no ISP’s that can collect data — the network is peer to peer. The code is free and open source. There are no exit nodes. Anyone can join and participate in the network. Can individuals scan sites or insert malicious code into their sites? Yes, and that is something that happens on any network.
There is ongoing research into how I2P network participants can be “deanonymized.” That is a good thing, because once the project understands how that may happen, they can address the issue and strengthen the network defences where needed.
There will always be attacks, there will always be vulnerabilities. Every network, every application, every user needs to be prepared for this. It is part of being online and creating the means for people to be online.
The I2P Java software comes preconfigured with privacy settings ( hops ) set in a way that optimizes the speed of your network experience. This means the highest level of protection without sacrificing experience. If a person needs or wants to add more protection to their communication they can, with the caveat that more hops can mean more latency in the time it takes for communications to traverse the network.
All the best engineering efforts need to be paired with proper OPSEC to achieve the best data and identity protection.
Who Uses The I2P Network?

Actually, we don’t know unless they tell us.
People have shared specific use cases, people have shared mundane use cases. The reason people use the I2P network is personal and unless they want to share their work, thoughts, art, or invite you or me to a forum, nobody will know or only people they want to know will know.
This is comparable to choosing not to have a site indexed on the clearnet. A close friend used to host a site of travel photos that they only shared with close friends and family. It was a way to bypass having to choose a social network that would interact with the data they shared in a potentially harmful way and also allow any stranger to see their photos. Because yes — what you share and how you share it matters. Free social platforms are not free, and sadly people target people online.
What a person shares is their choice. Yes, you can bring your clearnet identity over to the I2P network and set up a site with your travel photos, home decor, cat pictures — the choice is yours. There will be the benefit of all of the transports and encryption for your experience, and if you register your site, people can enjoy your photos while not being tracked or observed.
Mapping Your Threat Surface
Plainly speaking, if you do not want to keep track of where it is and who can access it, don’t do it.
This includes but is not limited too:
- Passwords
- Social forums
- Finances
- Assets ( art, business identity, logos)
Considering:
- What is the personal / financial impact of stolen data
- What is the longterm impact of persistent data imprints?
- What is the impact of data that is stolen or disclosed?
Keep track of what profiles you maintain and what services you interact with no matter what network you use. Perform personal risk assessments.
Message transport protection from interception is vital and provided by the network. Once that data arrives, it is in the hands of your own circle of trust and security. No overlay network is built to protect you from yourself.