Meet Your Maintainer: I2P Metrics
A conversation with Nguyen Phong Hoang and a look back on the research behind I2P Metrics.
In 2018 research was conducted to assess blocking access to the I2P site and reseed servers. In 2019, I analyzed data to support the research efforts to find blocking of the I2P website. At the end of the year I attended FOCI where Phong presented the research results. I2P Metrics continues to provide valuable I2P network insight.
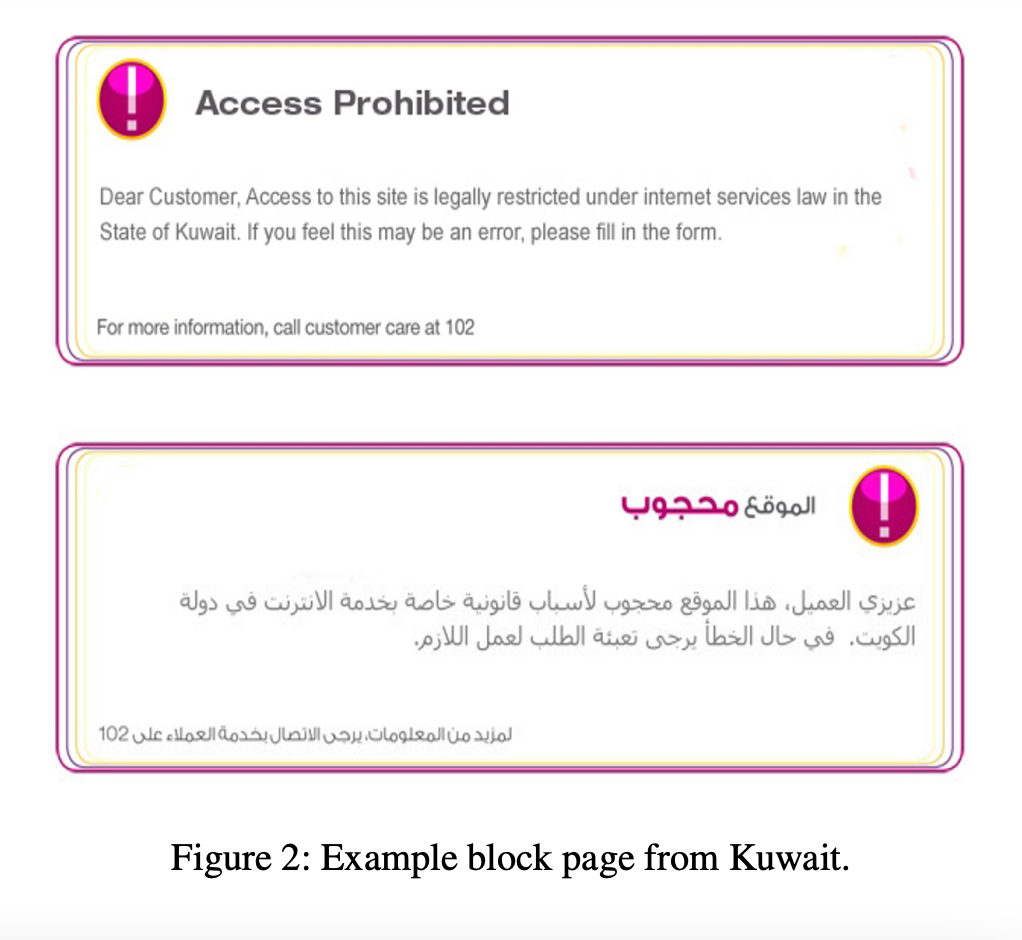
By conducting 54K measurements from 1.7K vantage points in 164 countries during a one-month period, it was found that China hindered access to I2P by poisoning DNS resolutions of the I2P homepage and three reseed servers. SNI-based blocking was detected in Oman and Qatar when accessing the I2P homepage over HTTPS. TCP packet injection was detected in Iran, Oman, Qatar, and Kuwait when visiting the mirror site via HTTP. Explicit block pages were discovered when visiting the mirror site from Oman, Qatar, and Kuwait. https://www. .org/system/files/foci19-paper_hoang.pdf
Nguyen Phong Hoang, Sadie Doreen, Michalis Polychronakis Measuring I2P Censorship at a Global Scale
Potential Solutions to Blocking
Since more and more oppressive regimes attempt to prevent local users from accessing the Tor network, Tor provides users in such restricted regions with a set of special relays called bridges [61]. Similarly, I2P can adopt the use of bridges to help those restricted users to access the network, along with a non-fingerprintable traffic pattern currently in development [35]. While the Tor community may have a difficult time recruiting bridges because new bridges are often found and blocked quickly [13], I2P has a higher potential to adopt the use of bridges because of the high churn rate of its dynamic and decentralized network. Despite the high blocking rates shown in Section 6.2, we notice a portion of peer IP addresses could not be blocked. These IP addresses often belong to newly joined peers. Therefore, a potential solution is to use these peers as bridges for restricted users. Since these peers are newly joined, they are less likely discovered and blocked immediately by the censor. Utilizing newly joined peers as bridges, however, may only be suitable for censored users who need to access I2P for a short period of time. If the peers stay in the network long enough, they will be discovered by the monitoring routers of the censor and eventually will be blocked. A potential approach to remedy this problem is to use newly joined peers in combination with the firewalled peers discovered in Sections 5.1 for a more sustainable censorship circumvention. https://arxiv.org/pdf/1809.09086.pdf
Nguyen Phong Hoang, Panagiotis Kintis, Manos Antonakakis, and Michalis Polychronakis. 2018. An Empirical Study of the I2P Anonymity Network and its Censorship Resistance.
About I2P Metrics
https://i2p-metrics.np-tokumei.net/
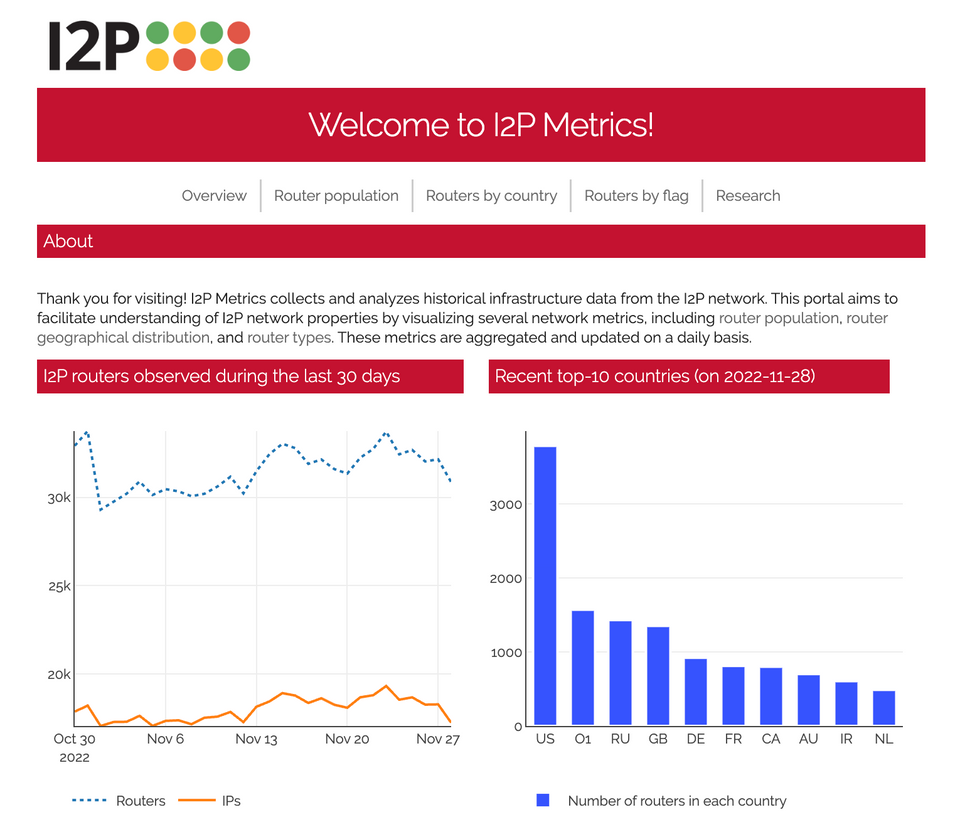
I2P Metrics collects and analyzes historical infrastructure data from the I2P network. This portal aims to facilitate understanding of I2P network properties by visualizing several network metrics, including router population, router geographical distribution, and router types. These metrics are aggregated and updated on a daily basis.
Can you tell people a bit about how you became interested in I2P?
When discussing anonymity networks, Tor and I2P often come into the picture as ones of the most popular anonymous communication tools. In addition to online anonymity and privacy, these tools by design can also be used to help at-risk people in repressive regions of the world to access censored contents as well as combating online surveillance.
Coming from a region notorious for suppressing the freedom of expression, I have been interested in anonymous communications in general, and I2P is one of those that catches my attention because of its ability to function as an alternative communication channel for censored users living in regions where the Internet is heavily restricted.
What did you learn from your research about I2P and its capabilities?
Despite the decentralized design of I2P, there are still some centralized elements such as reseed servers which can be used to throttle the initial joining phase of first-time users as discussed in this work (https://www.usenix.org/conference/foci19/presentation/hoang). In addition, the support of out-proxies is very limited. If the project can find more supportive organizations that are willing to operate out-proxies, I believe that I2P can be very useful for Internet users who live in repressive regions.
What services do you maintain?
I2P Metrics and a reseed server can be found through this tutorial: https://homepage.np-tokumei.net/post/notes-i2p-reseed-over-cloudflare/.
What can you say has changed or has evolved with regards to information blocking and restrictions?
As the Internet has become an indispensable medium for our daily communications, more and more authoritarian governments around the world are increasingly making use of different technologies to control the free flow of online information. Notorious censors include China, Iran, and Russia, having been in an arms race with the Internet freedom community, are continuously developing new technologies for Internet filtering at scale.
Have you observed any changes in router population or correlation to internet blocking?
Yes, Iran is one of the recent cases: https://twitter.com/np_tokumei/status/1573704554406977536
Glossary
Reseed: Reseed hosts are needed for your I2P router to to join the I2P network.
Outproxy: An outproxy is similar to Tor’s exit nodes, it allows for clearnet (normal internet traffic) to be relayed through the I2P network. In other words, it allows I2P users to access the internet through the safety of the I2P network.
Domain Name Blocking: This is a strategy for making it difficult to locate specific domains or websites.
TCP Packet Injection: This involves the injection of packets to block connections to censored websites.
Block Pages: A block page is an overt message to a user that a site is being censored/ blocked. The censor can redirect a query to a block page that will present the user with a message that access is denied or prohibited.