I2P Java Outproxy Workflow: New User Testing and Evaluation Using I2P In Private Browsing Mode On MacOS
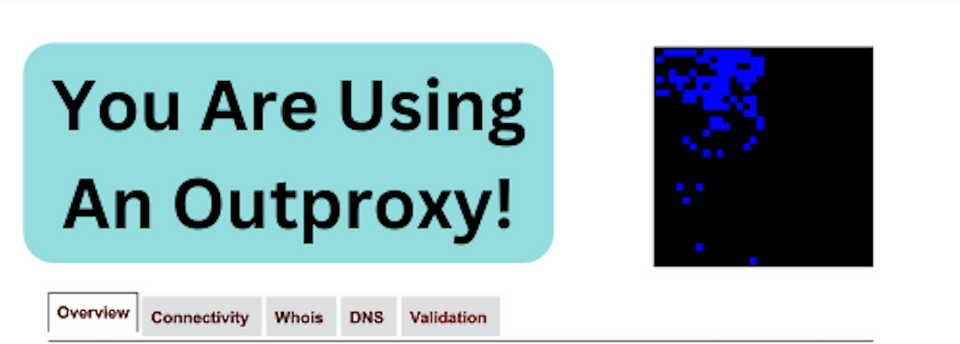
One of the most popular services for new I2P participants is the outproxy function. The outproxy service is not hosted or maintained by the I2P project. it is a third party service. Last year, the I2P core Java software team made the decision to include a new service operator called Stormycloud as the official outproxy service provider.
For people not familiar with what an outproxy is, its function is to handle clearnet requests through I2P. The request ( ie. reddit) is handled by the outproxy service rather than your own IP. This allows I2P participants to access sites on the Internet( "clearnet" ) with privacy. While the project has always encouraged its participants to use Tor Browser for this utility, it also understands that some people prefer maintaining a full I2P workflow.
The Volunteers
In December I met with a group of people who were privacy aware. Their own privacy and security actions included using two-factor, ensuring that app access was restricted, using care with posting to social media, and understanding brand and reputation threats. Not one person used Tor Browser, everyone used a VPN, three people used Signal, and there was no person who used a YubiKey or PGP. For mail providers, MailEnvelop and Proton mail were used, or Gmail with two-factor.
The Task
We walked through installing the I2P core Java software on MacOs with the goal of using the outproxy. After installing the router software, we all added the I2P In Private Browsing Mode add-on for the Firefox browser. This add-on creates a configuration free connection to the I2P network and is compatible with the outproxy.
Feedback
People were confused and looking for a specific workflow and verification that they were in fact using the outproxy. Since it is a browsing function, people expected to see evidence that they were using it in the browser with a visual element.
Some people thought that just because they were using I2P and entering searches that they were using it. It was not obvious in the extension how or where to access the outproxy. Some people tried to use the Legwork query option that said Proxy next to it. Not one person was successful in using the outproxy and found the task frustrating. People voiced concern for configuration issues that could lead to people making the mistake that they were actually using the outproxy. This was especially troubling for people who may be searching for information that is being surveilled or illegal (abortion information, or looking for resources for finding protection from an abuser).
"Considering the mindset I would be in if I was a situation where I would need something like this, I think I would become very anxious."
"People are used to visual cues that they are using something - I can't even tell where I am supposed to start."
"I saw instruction that I can just browse, but how? How can I tell if I'm using it?"
With no verification or obvious secure configuration, people felt uncomfortable and frustrated by the process.
Ideas For Ease of Use
Working with the volunteers, I demonstrated how to get to a site using the outproxy.
Clicking on the I2P In Private Browsing Mode icon in the browser toolbar accesses the browser function panel. Here people were looking for the outproxy. They were looking for something to open in the browser.

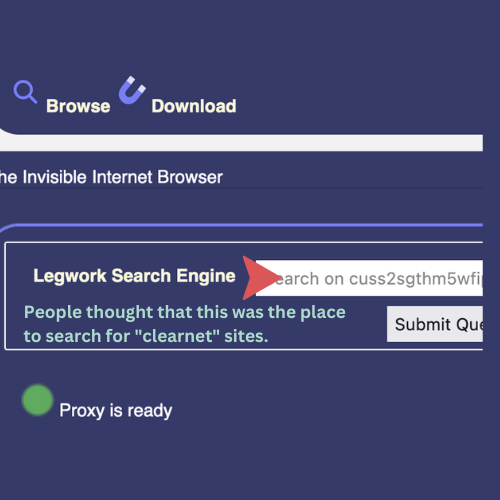
Some people became confused with terms ( outproxy/ proxy) and thought that they could search here.
This section is for accessing I2P network sites however.
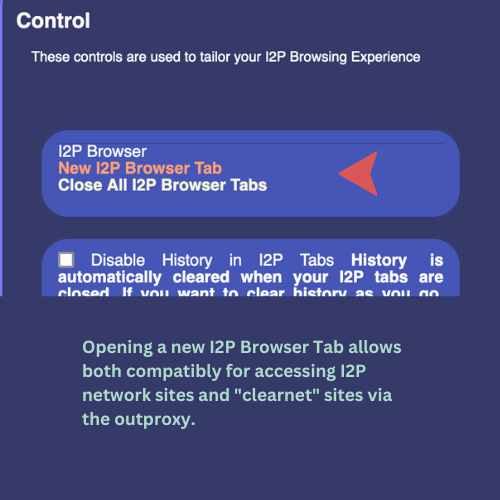
Here is where people can open a tab that will allow either I2P or "clearnet" access. It might be a consideration to add "Access outproxy and proxy in this tab" to the section.
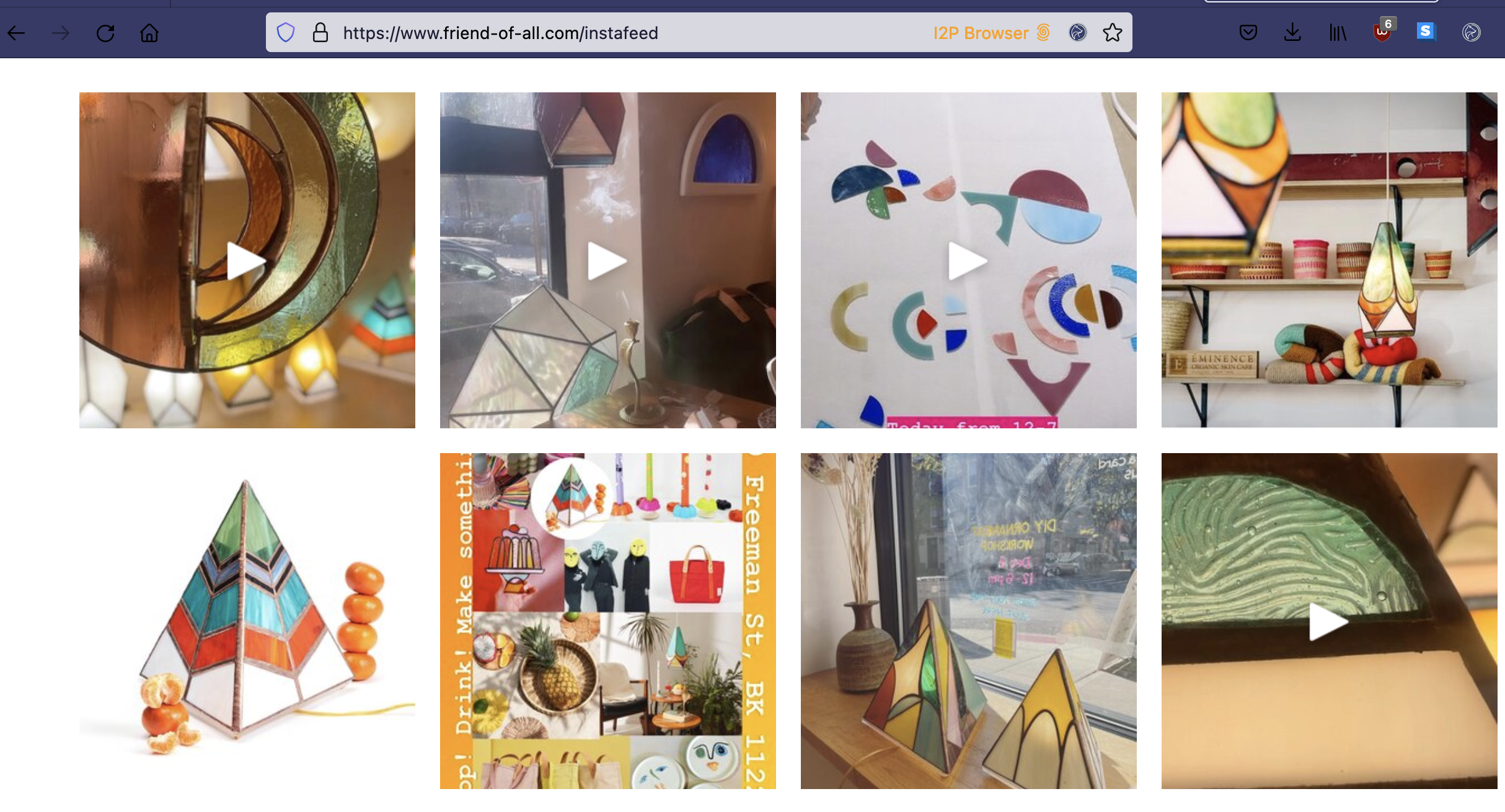
A successful visit to a stained glass shop. We did this on my laptop where I also have other extensions installed, as seen in the screenshot.
The volunteers were able to see loading errors and performance differences as well.
Everyone very quickly understood how to use the outproxy and the container function of the browser add-on after a walkthrough. Some felt it was too much for their own privacy threat model, but could see use cases where it would be required and valuable to use.
Verification For Peace of Mind
Since an outproxy conceals your IP and creates the connection to the "clearnet" site on your behalf, one of the only ways to make sure that your tab is using the outproxy is to check if it is your own IP or the service making the request.
I2P in Private Browsing Mode does handle this visually by using a dark purple container for browsing. However, if a person wants to do this for their own security to verify that the search in that tab is being handled by the outproxy, they can compare IP and DNS using BGP Tools https://bgp.tools/. This is also useful for people who want to configure their own I2P browsing experience.
It may be a consideration to add a link to BGP tools so that a person can verify that the are using the outproxy with an agreed on data set to check against with the service provider. Perhaps Stormycloud could add a "check outproxy" page.
In the meantime, a step by step guide will be created for people who are new to the I2P network.
Conclusion
The I2P in Private Browsing Mode add-on for Firefox has ease of use and secure workflow built in, but some of these functions were not obvious. The outproxy functions perfectly, but its relationship with I2P in Private Browsing Mode was not obvious to the volunteers.
With guides and a few UX changes we should be able to create a more clear relationship and include ways to verify configuration and connection.
The I2P in Private Browsing Mode add-on provides the best browsing experience for the I2P network. You can get it here: https://addons.mozilla.org/en-US/firefox/addon/i2p-in-private-browsing/
Stormycloud provides outproxy services for the I2P network https://stormycloud.org/i2p-outproxy/.
The I2P Secure Design Collective works with volunteers, developers and service operators to provide feedback and solutions for successful adoption and onboarding to the I2P network. https://github.com/Shoalsteed/I2P-Secure-Design-Collective